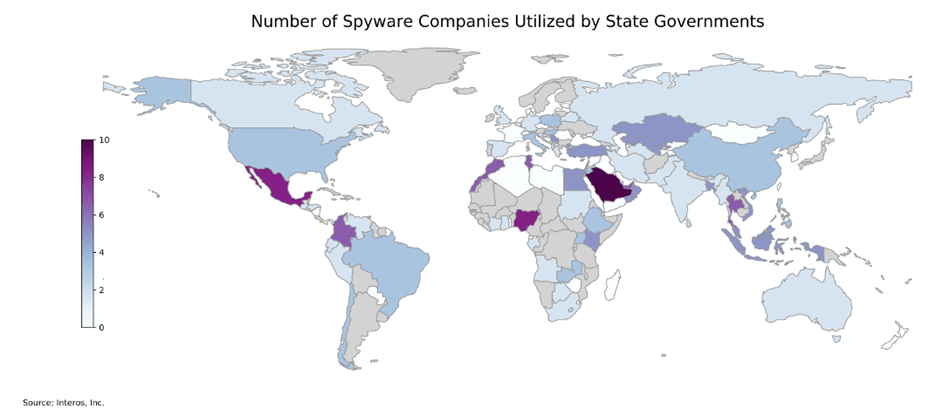
How Vulnerable Are We to Commercial Spyware?
October 24, 2024Feature Article(Source)
Commercial spyware is malware developed by private corporations that effectively repurposes users’ devices into surveillance tools. Once it gains access, commercial spyware can harvest any data on the device and transmit it. This not only includes the device’s stored data but also information collected from remote activation of its cameras and microphones without the user’s permission or knowledge. Governments are simultaneously supportive and wary of this technology as it presents both a national security boon and threat. Currently, U.S. law affords little certainty in protecting private citizens who are victims of commercial spyware. The infamous Pegasus spyware, developed by the NSO Group, is the posterchild of commercial spyware.
What is Pegasus?
Pegasus is capable of covertly infiltrating a variety of smartphone operating systems, including iOS and Android. It can harvest data or collect data through the target phone’s camera, microphone, and apps. Concerning U.S. personnel abroad, Pegasus surveillance previously targeted U.S. embassy staff in Uganda and a high profile U.S. diplomat. Other targets include American journalists, aid workers, and businessmen.
Unlike PRISM, the infamous NSA spying program exposed in 2013 by Edward Snowden, Pegasus surveils more upstream data, closer to the source. In contrast, Prism used backdoor access to the servers of vendors, such as Facebook and Google, scouring stored e-mails, videos, and voice chats.
How does Pegasus work?
Pegasus infects your phone through zero-day and zero-click exploits. A zero-day takes advantage of a yet unknown security flaw. The name comes from the fact that there are zero days to patch the vulnerability before it is used. Zero-clicks are a type of zero-day that does not require any user input to infect the user’s device with malicious software, unlike a typical phishing attack that lures users into clicking on a malicious link.
Software companies offer rewards, known as bug bounties, in exchange for zero-days, which lets them patch the vulnerabilities and keep their products secure. However, both software companies and commercial spyware developers compete against each other for zero-days. And currently, the commercial spyware companies are winning. In other words, the market for zero-days has shifted in favor of commercial spyware developers.
What was the United States government’s response to Pegasus?
In July 2021, a leaked list of prospective Pegasus surveillance targets included American journalists, aid workers, and diplomats. In response, the NSO Group made assurances that the spyware was incapable of targeting American phone numbers within the United States. In December 2021, the U.S. Department of Commerce blacklisted the NSO Group for malicious cyber activities because of Pegasus spyware discovered on the phones of U.S. State Department employees in Uganda. Subsequently, the New York Times revealed that the FBI purchased Pegasus in 2019 and tested it alongside another commercial spyware, one capable of deployment against American phones. In March 2023, President Biden signed an executive order prohibiting the United States government from using commercial spyware that poses a risk to national security. Notably, the U.S. does not rule out the use of commercial spyware against private citizens. In fact, the United States, along with other nations, views commercial spyware as a necessary tool for national security that also represents a potential national security threat.
What are my legal protections?
Currently, cases involving Pegasus in the United States are limited. None have reached a judgment, and no case involves individual United States citizens. After Apple Inc. sought dismissal of its lawsuit against the NSO Group on September 13, 2024, only two cases involving Pegasus remain active in the United States. One case involves WhatsApp, which accuses the NSO Group of exploiting a bug in the messaging app to infect 1,400 devices with Pegasus. Another involves El Faro, an El Salvadoran news organization targeted by Pegasus surveillance.
WhatsApp is arguing its case under the Computer Fraud and Abuse Act of 1986 (CFAA). In 2021, Van Buren v. United States interpreted the CFAA’s idea of unauthorized access as akin to a traditional trespass. Essentially, accessing information via an unauthorized method or in an off-limits area gives rise to criminal and civil liability under the CFAA. If WhatsApp chooses to apply this theory and succeeds, then it is theoretically possible for any victim of a commercial spyware infection to file a claim.
However, significant challenges remain for litigating commercial spyware cases. Foremost, plaintiffs must be able to establish standing by suffering concrete and particularized injury. Secondly, it is unclear if commercial spyware companies are ideal defendants considering that their customers, state governments, are the ones doing the actual spying.
In sum, individual legal protections against commercial spyware remain indefinite: much hinges on the outcome of WhatsApp’s lawsuit and the general applicability of Van Buren’s interpretation of the CFAA. Future litigation will present more answers, but it remains to be seen if the law can keep abreast with the proliferation of sophisticated commercial spyware.
What about the future?
The lack of successful litigation against the usage of commercial spyware means that, for the moment, potential litigation by American citizens must rely on novel legal theories. A win by WhatsApp would potentially give Americans a singular but potent arrow in their quiver.
On the other hand, altering the current status quo of government surveillance requires legislation. In fact, the Government Surveillance Reform Act (GSRA) of 2023 proposes to do just that by closing several surveillance loopholes that enable warrantless searches for Americans’ communications and data. While not yet enacted, the bipartisan bill would bolster and modernize Americans’ privacy rights.
All told, while the availability of definite legal solutions leaves much to be desired, progress means that leaving our phones behind is also no longer our only option.
Suggest Citation: Michael Ahn, How Vulnerable Are We to Commercial Spywares?, Cornell J.L. & Pub. Pol’y, The Issue Spotter (Oct. 24, 2024), http://jlpp.org/how-vulnerable-are-we-to-commercial-spyware/.

Michael Ahn is a second-year law student at Cornell Law School. He studied economics as an undergraduate and earned his MA in Economics before pursuing a law degree. He previously worked as a senior research assistant for the Board of Governors of the Federal Reserve System.
You may also like
- November 2024
- October 2024
- April 2024
- March 2024
- February 2024
- November 2023
- October 2023
- April 2023
- March 2023
- February 2023
- January 2023
- December 2022
- November 2022
- October 2022
- May 2022
- April 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
- May 2021
- April 2021
- March 2021
- February 2021
- January 2021
- November 2020
- October 2020
- September 2020
- August 2020
- July 2020
- June 2020
- May 2020
- April 2020
- March 2020
- February 2020
- January 2020
- November 2019
- October 2019
- September 2019
- April 2019
- February 2019
- December 2018
- November 2018
- October 2018
- September 2018
- March 2018
- February 2018
- January 2018
- December 2017
- November 2017
- October 2017
- September 2017
- May 2017
- April 2017
- March 2017
- February 2017
- December 2016
- November 2016
- October 2016
- April 2016
- March 2016
- February 2016
- January 2016
- December 2015
- November 2015
- October 2015
- June 2015
- May 2015
- April 2015
- March 2015
- February 2015
- January 2015
- December 2014
- November 2014
- October 2014
- August 2014
- March 2014
- February 2014
- January 2014
- December 2013
- November 2013
- October 2013
- September 2013
- May 2013
- April 2013
- March 2013
- February 2013
- January 2013
- December 2012
- November 2012
- October 2012
- September 2012
- June 2012
- April 2012
- March 2012
- February 2012
- January 2012
- December 2011
- November 2011
- October 2011
- September 2011
- August 2011
- April 2011
- March 2011
- November 2010
- October 2010
- September 2010